First
Fallout Exploit Kit has been observed since August 2018. It is very popular and used in many attack campaigns. However, around the end of 2018 Fallout was no longer observed. It was a short break, he came back soon.He came back and contained several changes.
1. HTTPS
- Using Let's Encrypt
2. Landing Page
- Changed code to generate code for exploitation
3. CVE-2018-8174
- Changed shellcode
- Using PowerShell
- Bypass AMSI
4. CVE-2018-15982
In this article, I will look into these changes in detail.
HTTPS
Fallout began using HTTPS. This may make analysis and detection a bit more difficult. He uses Let's Encrypt.Landing Page
JavaScript was not obfuscated in the previous landing page. Custom Base64 for generating exploitation code was easy to read and the table was written as it was.All such processing is obfuscated in the new landing page. But you don't have to be afraid of it. Its obfuscation is very simple.
If you take out the last JavaScript and decode it, it looks something like this.
It will look like this if you clean it up.
Let's read in turn. The first line extracts necessary data from HTML. Decode this string to generate exploitation code. The second line defines the table of Custom Base64.
The next two functions are Custom Base64. This has not changed since the past.
Next Fallout is creating an embed element. Although src is encoded, it becomes a URL by decoding it. This reads the exploitation SWF of CVE-2018-15982.
Finally Fallout is creating a script element. VBScript text is the decoded version of HTML data read in line 1. This reads the exploitation code of CVE-2018-8174.
CVE-2018-8174
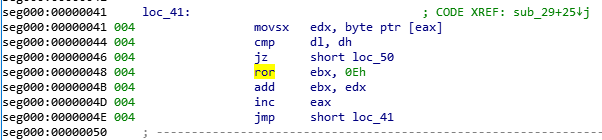
The code is exactly the same as PoC. shellcode has been updated.Looking at shellcode, it contains encrypted data at the end. Run it on CreateProcessA.
Data is encrypted by RC4.
The key is hard-coded, and when you decode it using it, you get such PowerShell code.
Decoding Base64 and formatting it look like this:
The first line is a technique to Bypass Anti Malware Scan Interface. Matt Graeber tweeted in 2016.
Next, the C # code is defined. When it shapes it, it looks like this. This will define CreateProcess.[Ref].Assembly.GetType('https://t.co/Kwfd9odrBv.Automation.AmsiUtils').GetField('amsiInitFailed','NonPublic,Static').SetValue($null,$true)— Matt Graeber (@mattifestation) 2016年5月25日
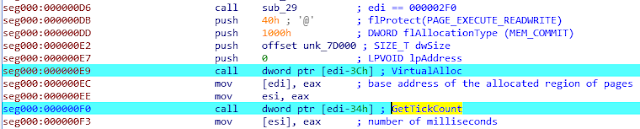
Next is the process of downloading and saving malware. Previously it was encrypted with RC4, but now it is an exe file.
Finally, run the malware by CreateProcess.
CVE-2018-15982
In this update CVE-2018-15982 has been added to Fallout.However, this is the same as PoC. Shellcode is the original but it is the same algorithm as the one already explained in 8174.
It is slightly different only in the final PowerShell code. Instead of executing malware with CreateProcess like 8174, it is running with Invoke-Expression.
Conclusion
Fallout made an interesting update such as exploiting CVE-2018-15982, downloading and executing malware with PowerShell by bypassing Anti Malware Scan Interface. 15982 has also been exploited in other exploit kits such as Underminer. Please pay attention to them.Sample Data
- saz
- 8174
- a821dda3cba7851bf0baf4bce8da04d78107be846b18bcb6d29dc92d49973ca8
- 15982
- 71fcea2737551627e5bd9968903f68b7cb81a75b92fa9d10c767c1b23e6084ac
- swf
- 15982
- e82b042f438c173ae90d056a6c52c0a822d0f263bf8abab60503b9c5c6d68a9c